
The episode: 169 – Passwordless med Yubikey
Recorded: 2022-05-10 (publicerat 2022-05-15)
Participants: Mattias Jadesköld, Erik Zalitis och Dain Nilsson.
This episode is made in cooperation with Nordlo.
Listen to the episode, now – Yubikey
(This episode is wholly in English, except for the short intro message)
Raffle!
You want a Yubikey of your own? Yubico gave as five Yubikeys to give away to you in a raffle that runs between the 15th of May 2022 until the 29th of May 2022. All you need to do is to share this page on Facebook or Twitter. Or to like our Facebook group. Or on twitter: either follow us on twitter OR share our post regarding this episode on Twitter.
The winners will be announced on the 29th of October on our Twitter and Facebook-accounts. And on this website (www.itsakerhetspodden.se).
While listening to this episode – Yubico
So where to start? Probably when someone saw the need for passwords to keep stuff protected or the wrong people out of your speakeasy. And it has gone downhill from there. First we had identification, as in ”I claim to be this person”. Then authentication as in, ”I am this person, and here is something to prove that in fact I am”. The latter was until recently a password in the IT-industry. That is, something only you knew. You and all the hackers, that is.
The we asked you to created unique and super-complicated passwords that you forgot, then wrote on a piece of paper and put it under the keyboard. This was before it got really bad. Yubico was founded around that time and quickly grasped the problems that had to be solved.
Multi-factor authentication was sold as the final word in the argument about security. That is ”I claim to be this person, and here is a weird concoction of letters and number to prove I know something only you and I know. Oh, and here is a elektronic dohickey to make that super clear. You know, that it’s me….”
This was often followed by ”Oh dear, I forgot the device” or ”Hmm… I don’t remember the code to open it”.
In short, the medicine was sometimes worse than the disease.
Yubico and their solution
Yubicos solution started out as a simple remedy with a novel approach. When you put it in the USB-port it created a ”fake keyboard” in your computer that could send a preset password with a very high complexity and length. But this was limited, and with the adoption of standards like ”Webauthn”, it could then do much more secure authentication. This leads us into today.
What if you lose the device itself? This problem can be solved today with the same solutions used if you lose your passwords or your other MFA devices. Great, but all these solutions have their limitations. Listen to the podcast for a complete walk-through.
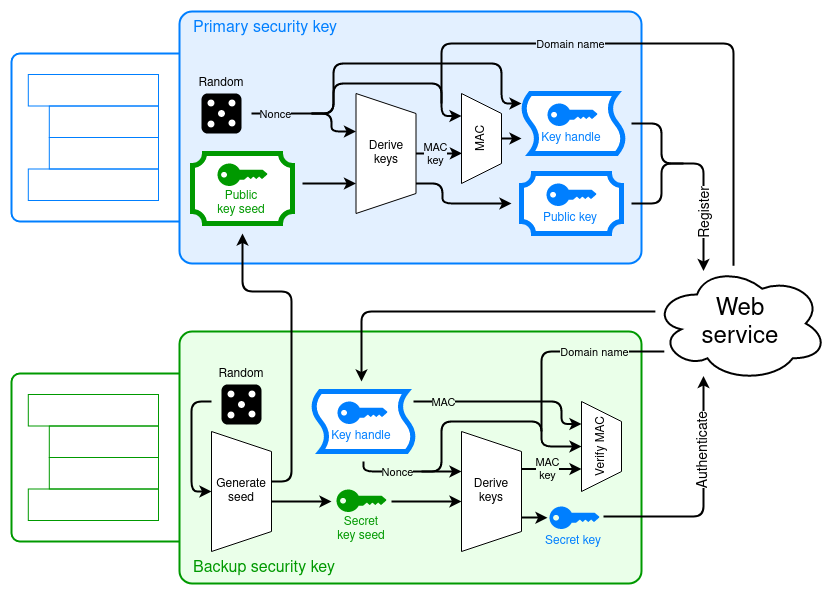
Yubico recommends a standard of their own making called ”Asynchronous Remote Key Generation” (ARKG) that both I and Mattias struggle to pronounce. Dain explains how this is meant to work in the podcast and I will just put this illustration here to aid you in understanding it. (As I, myself, apparently desperately need)
Links – Yubikey
Errors and omissions
- Mattias incorrectly claims this to be the 168th episode, when in reality it is number 169.
